Asset Inspection Software
Simple, Robust, Reliable.
Redefine safety. Conduct inspections in volume, maintain compliance, and empower your front-line with the latest mobile technology.
Book a Demo
Asset Inspection Software
Simple, Robust, Reliable.
Redefine safety. Conduct inspections in volume, maintain compliance, and empower your front-line with the latest mobile technology.

Increase Efficiency
Complete inspections and audits faster, more accurately, and without duplicate data entry

Reduce Liability
Automatic scheduling and notifications ensure work is done on time, reducing the chance of an accident

Maintain Compliance
The Field iD Safety Dashboard ensures complete visibility into your compliance requirements
Empower Your Workers
Show your workers you truly care about safety by allowing them to conduct adhoc audits to find potential hazards

Increase Efficiency
Complete inspections and audits faster, more accurately, and without duplicate data entry

Reduce Liability
Automatic scheduling and notifications ensure work is done on time, reducing the chance of an accident

Maintain Compliance
The Field iD Safety Dashboard ensures complete visibility into your compliance requirements
Empower Your Workers
Show your workers you truly care about safety by allowing them to conduct adhoc audits to find potential hazards
Connect your front-line with the boardroom
Product Features
Access Online or Offline
Field iD is designed to execute no matter where you are. Its reliable offline mode allows you to search for a range of assets and collect large volumes of data, without missing a beat. Whether you are working remotely or in-house, Field iD will deliver.
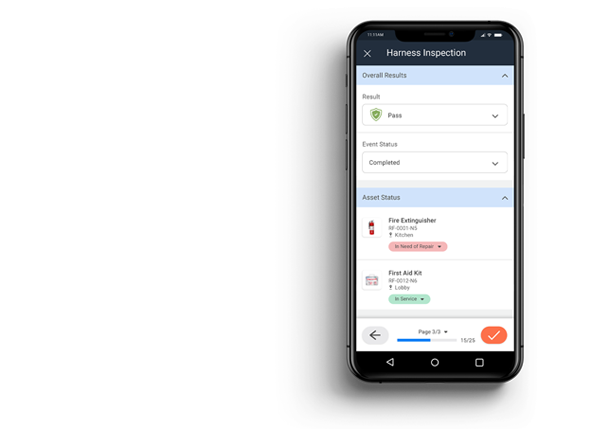
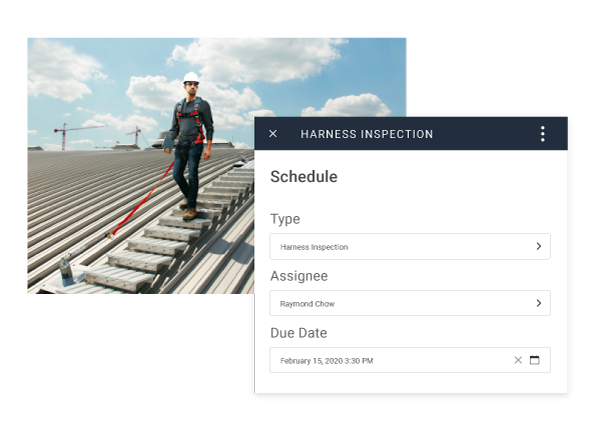
Digitize Equipment Inspection
Elevate your documentation with our powerful form builder, tailored to simplify custom inspection form creation. With the ability to automate inspections and perform them at volume, you can ensure an increase in efficiency and accuracy.
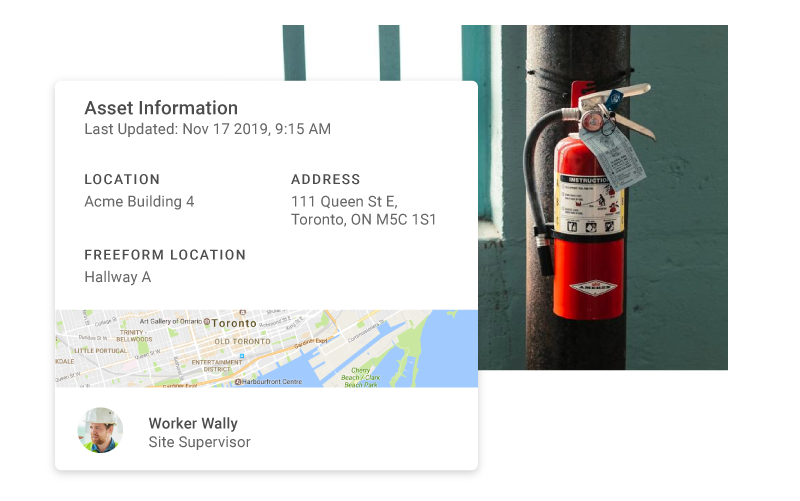
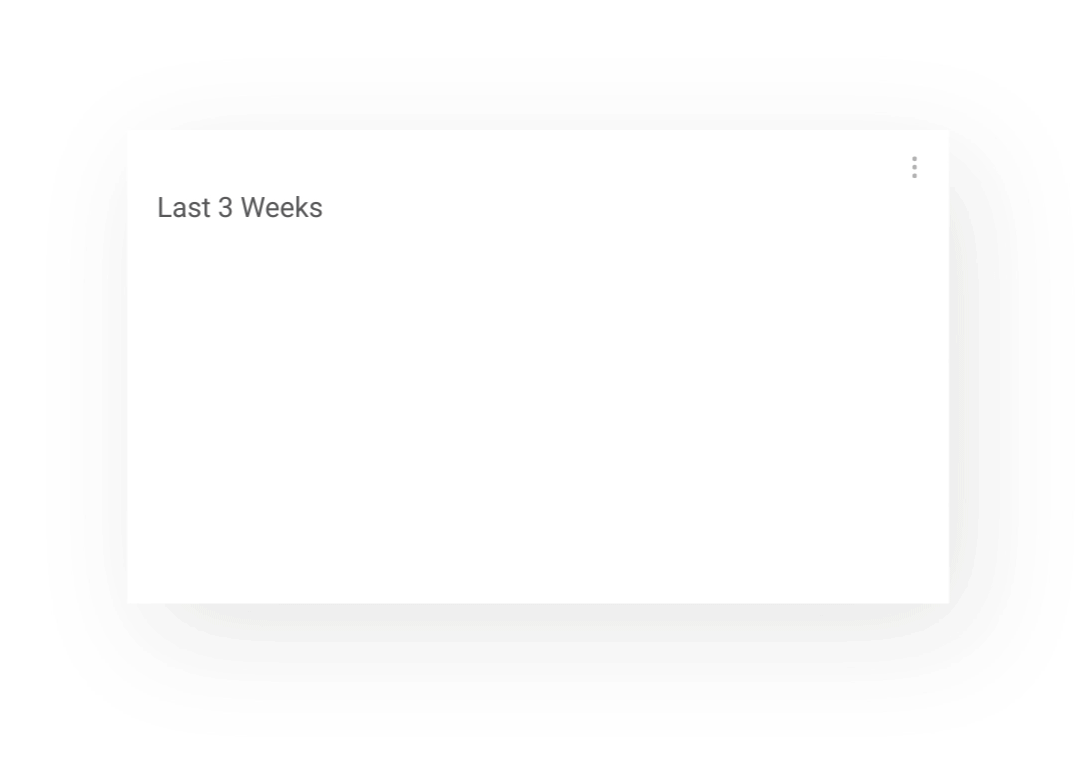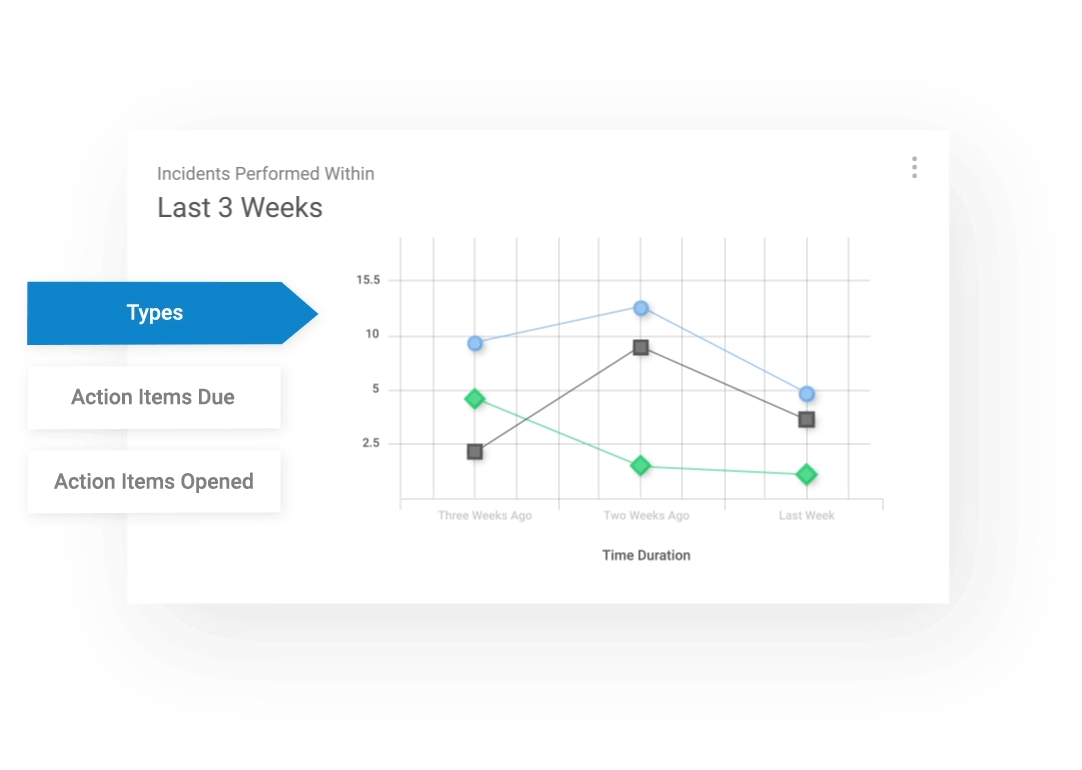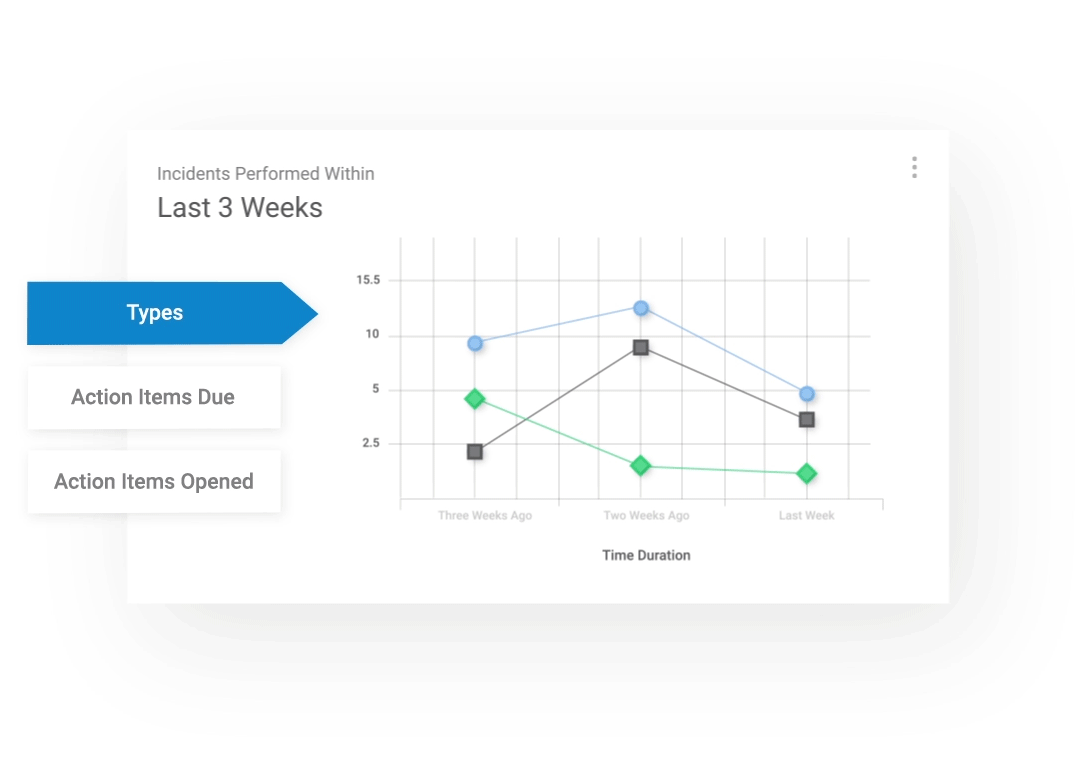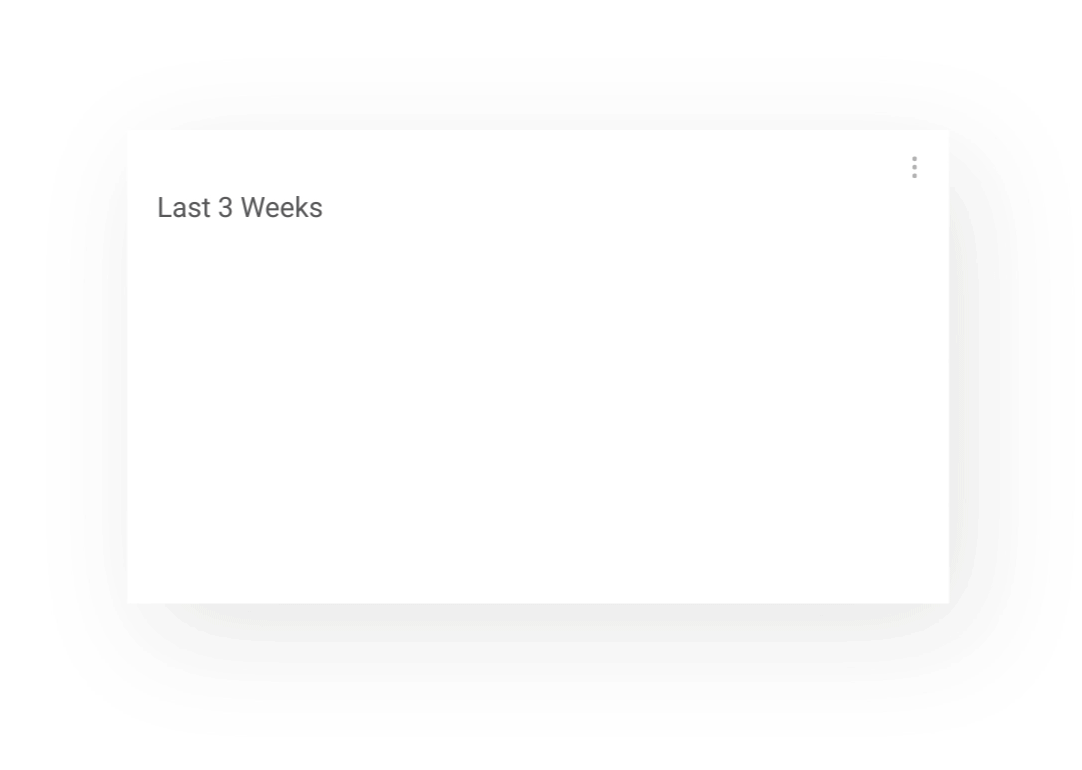
Get 360 Visibility
View the safety status of your organization in real time, with our powerful reporting functionality. With customized reports at a glance, you can always ensure compliance with safety regulations and be fully prepared for an audit.
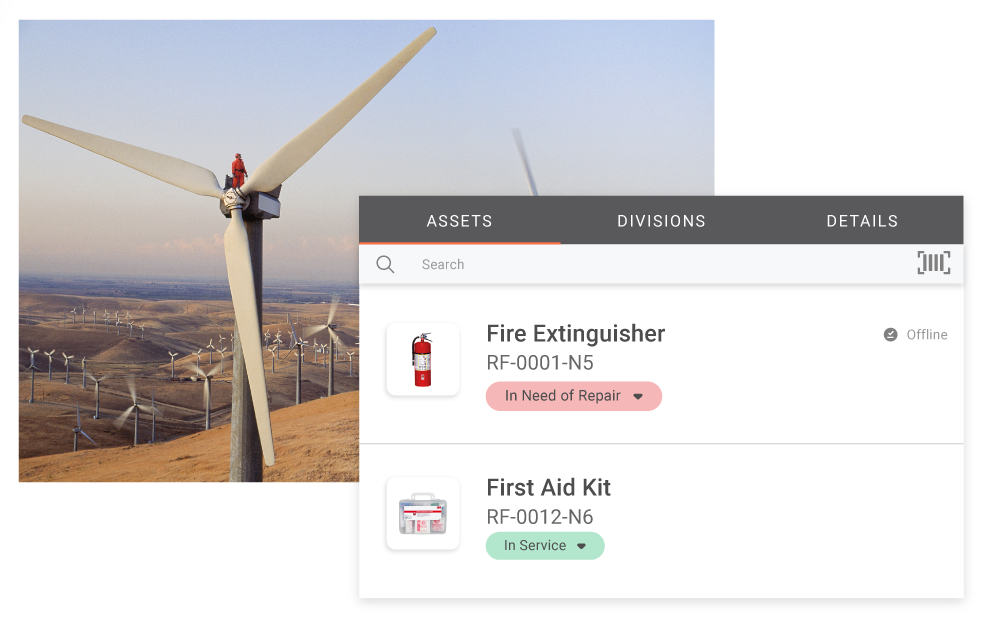
Optimize With Dynamic Features
The latest in RFID cutting-edge technology allows you to conduct inspections in volume with ease. Gain access to multiple tagging options and automatically centralize all data to maximize efficiency.
Product Features
Access On or Offline
Field iD is designed to execute no matter where you are. Its reliable offline mode allows you to search for a range of assets and collect large volumes of data, without missing a beat. Whether you are working remotely or in-house, Field iD will deliver.

Digitize Equipment Inspection
Elevate your documentation with our powerful form builder, tailored to simplify custom inspection form creation. With the ability to automate inspections and perform them at volume, you can ensure an increase in efficiency and accuracy.
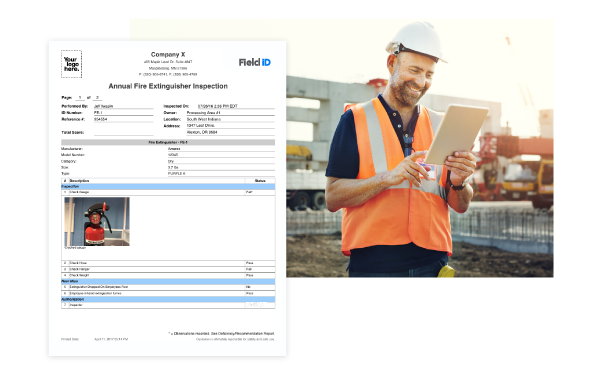
Get 360 Visibility
View the safety status of your organization in real time, with our powerful reporting functionality. With customized reports at a glance, you can always ensure compliance with safety regulations and be fully prepared for an audit.

Optimize With Dynamic Features
The latest in RFID cutting-edge technology allows you to conduct inspections in volume with ease. Gain access to multiple tagging options and automatically centralize all data to maximize efficiency.
Reduce property damage, lost/stolen tools, and prevent critical equipment failure with eCompliance’s equipment tracking Field iD™ technology.
 See how Delta Airlines used Field iD™ to eliminate injuries
and inefficiencies.
See how Delta Airlines used Field iD™ to eliminate injuries
and inefficiencies. Optimize Your Workflow
Access dynamic features
From scanning assets with high frequency RFID, 2D, or 3D barcodes to assigning and signing off on paperless forms, discover a range of features designed by experts in the field to strengthen your asset inspection processes.
*3-months free when you sign-up for 1-year, or more. Offer ends August 31, 2020.
